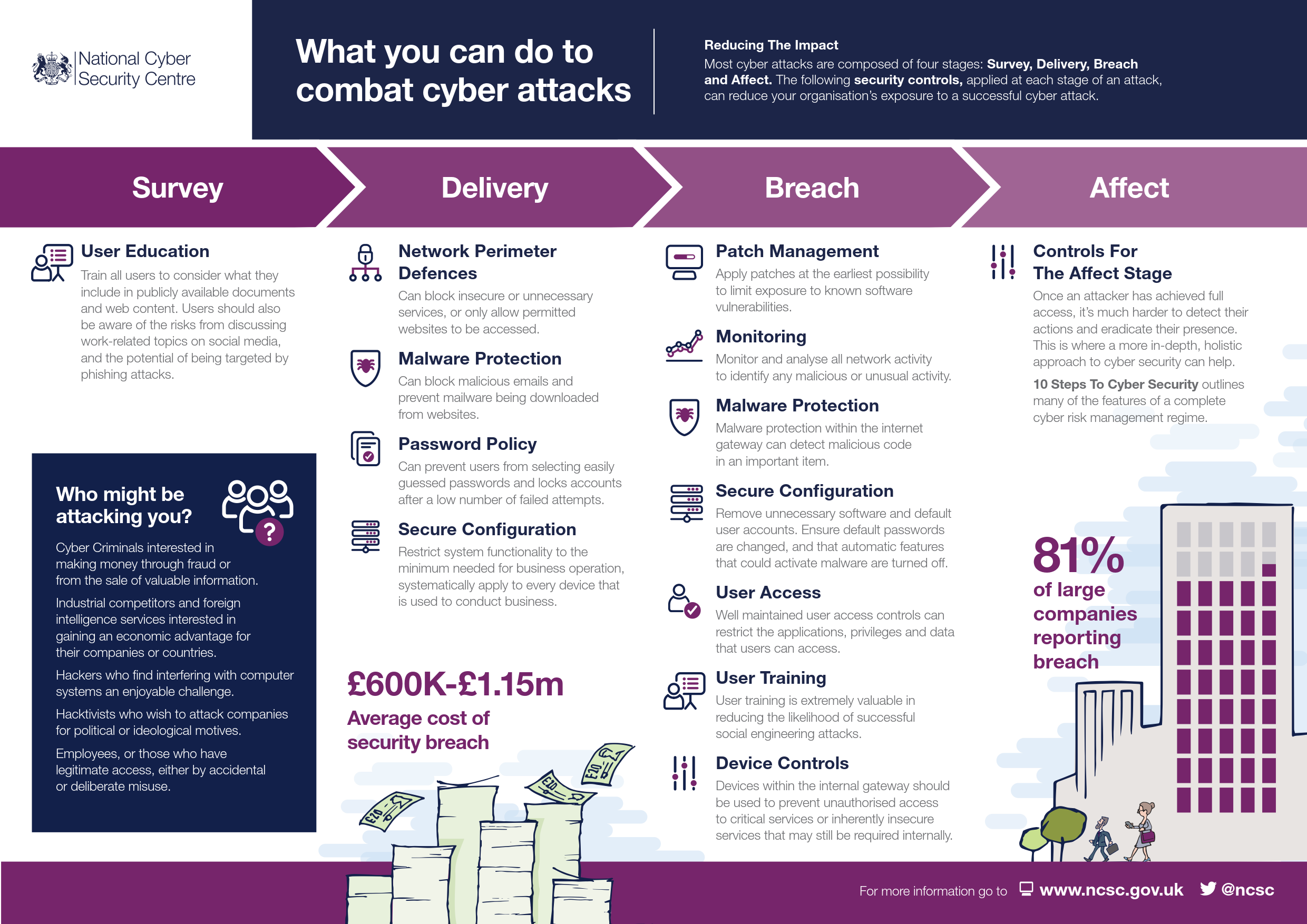
10 Steps to Cybersecurity During a Pandemic - The Fulcrum Group 10 Steps to Cybersecurity During a Pandemic

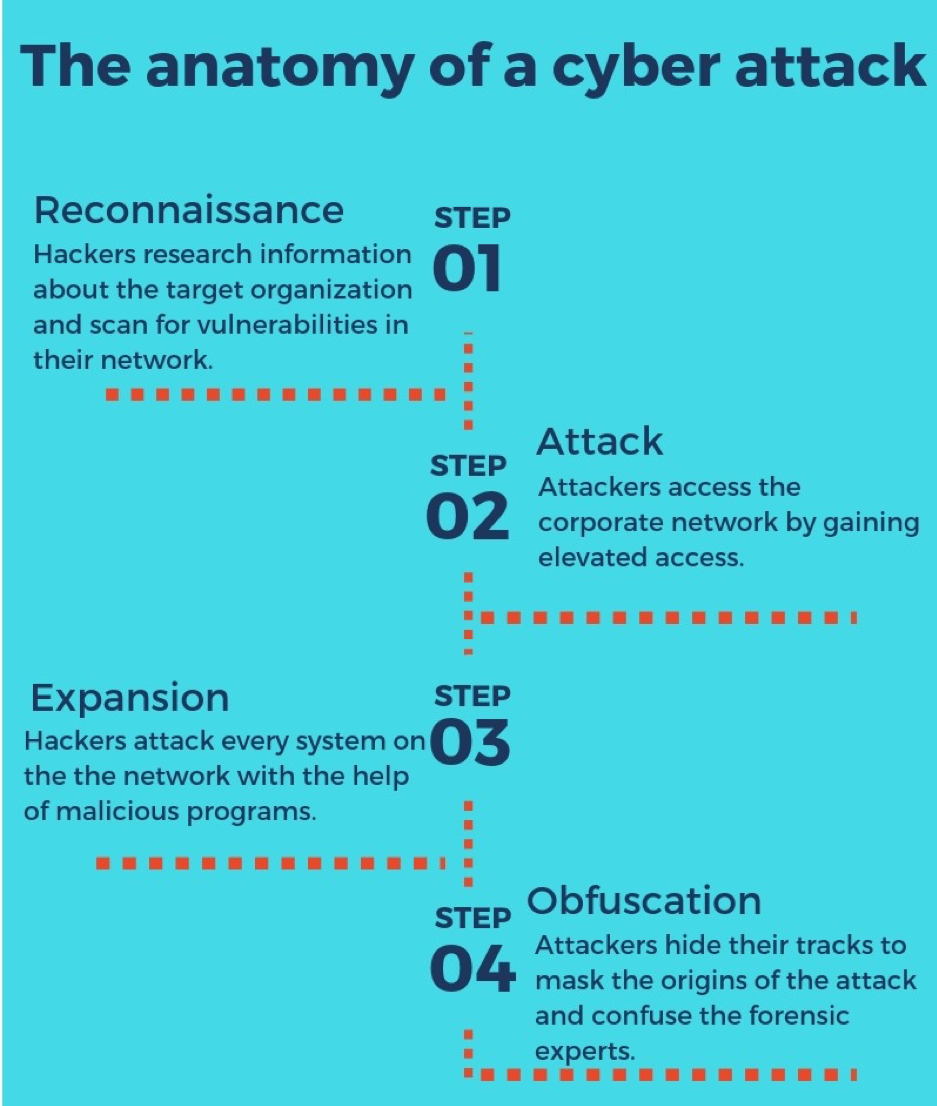
Cyber Security Feed on Twitter: "RT @hackinarticles: Cyber Attack Quick Response #infosec #cybersecurity #pentesting #oscp #informationsecurity #cissp #CyberSec #network…" / Twitter