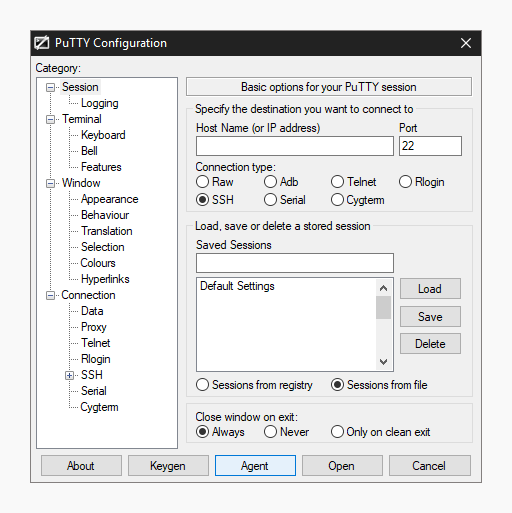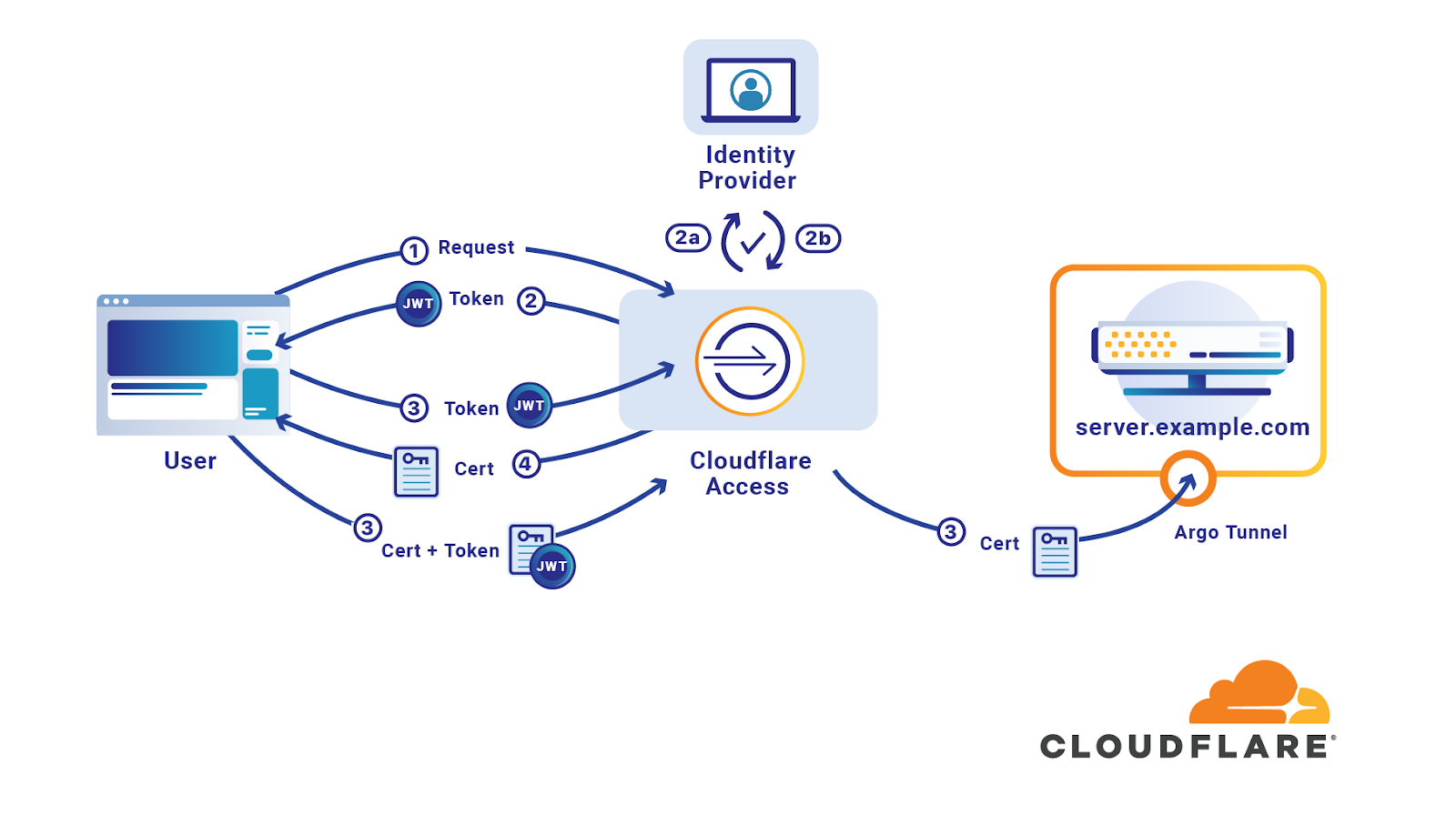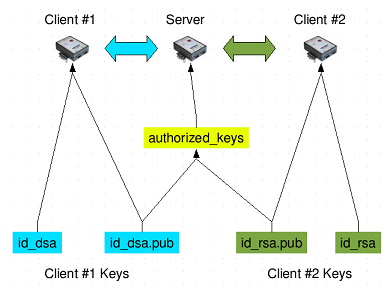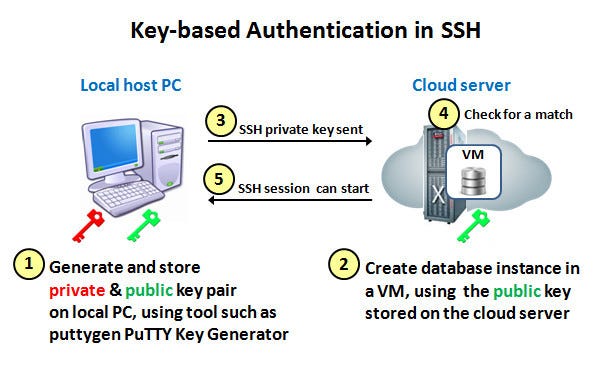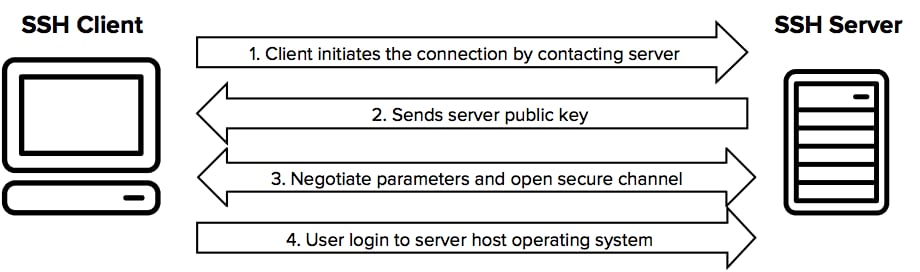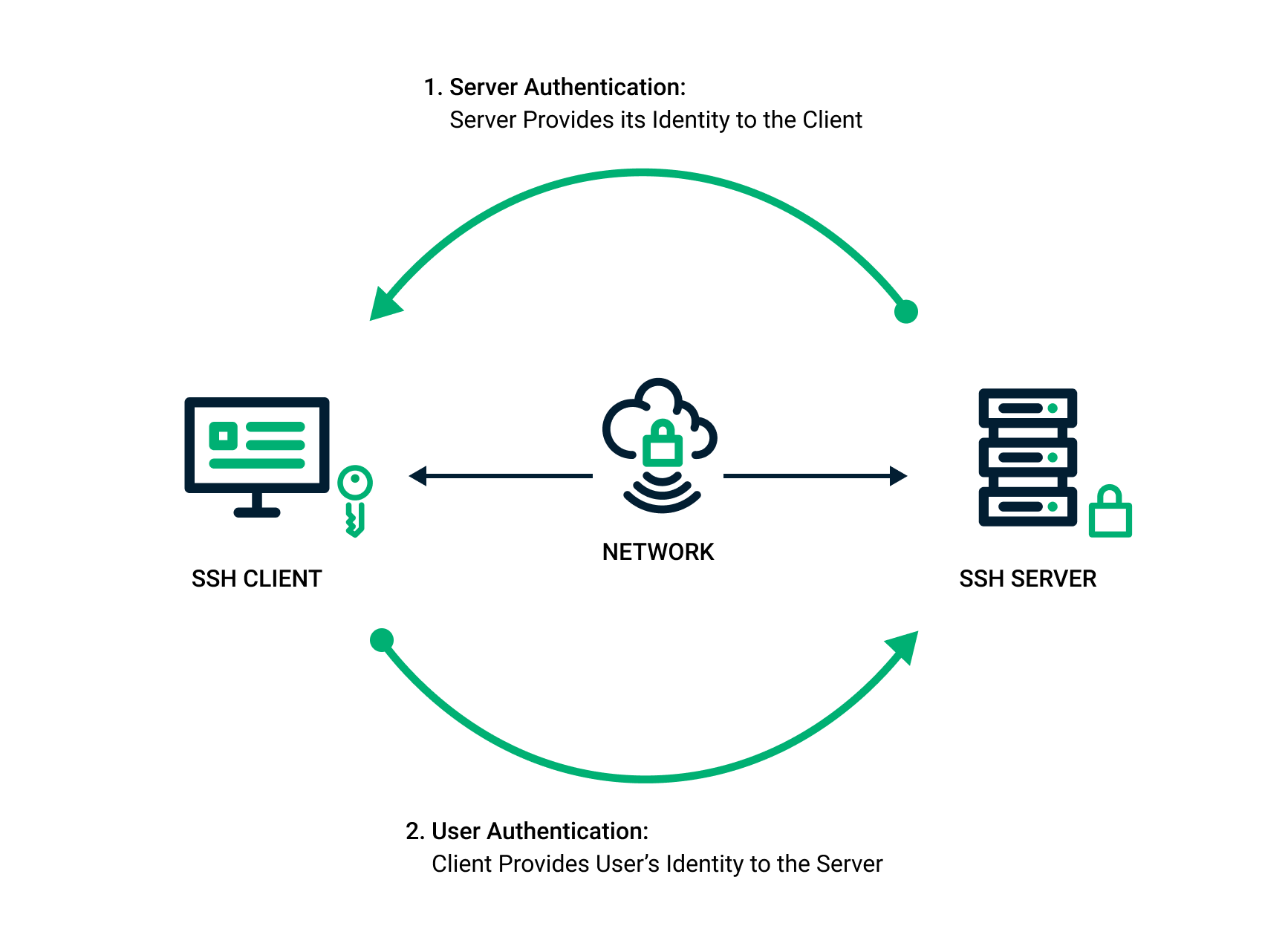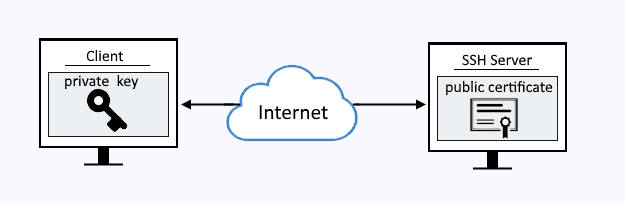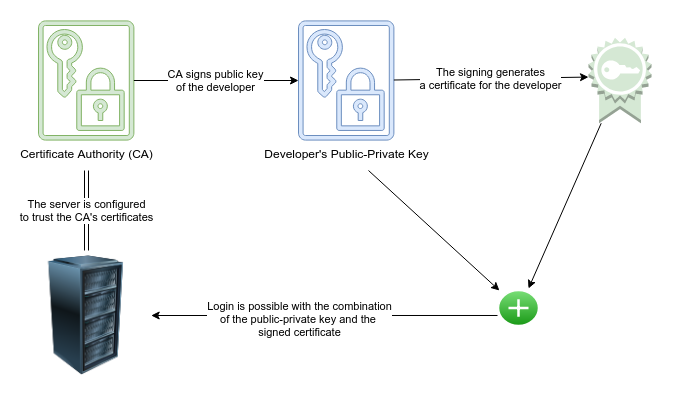
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples

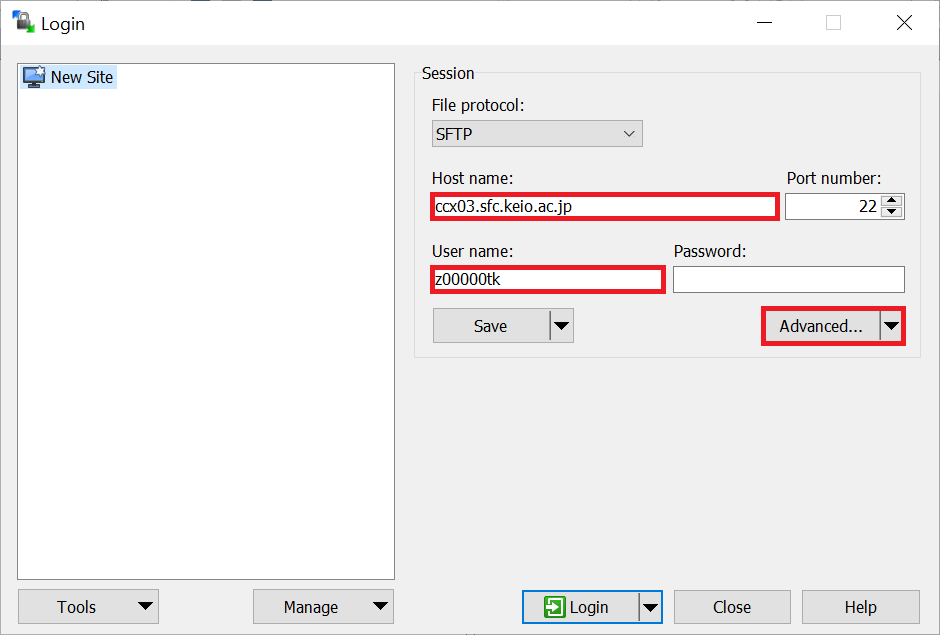
Generating key pair using PuTTygen, and setting up your public key to server | Zengaku Computer System, A.C.C.C., University of Tsukuba

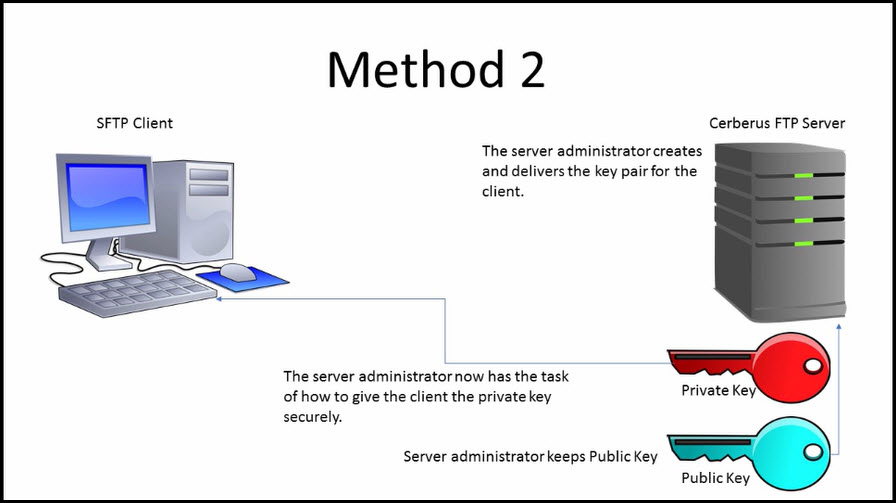


![How to SSH Through Bastion With Key [Tutorial] | strongDM How to SSH Through Bastion With Key [Tutorial] | strongDM](https://assets-global.website-files.com/5f1c75e63b2f950eb473d3e4/605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key.jpg)