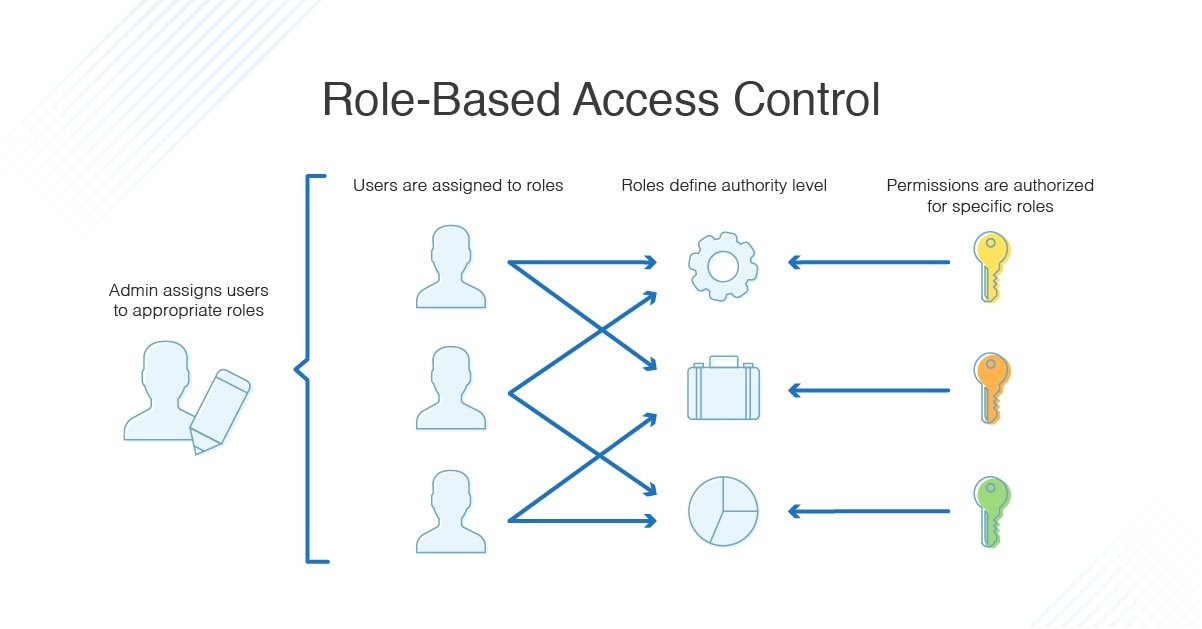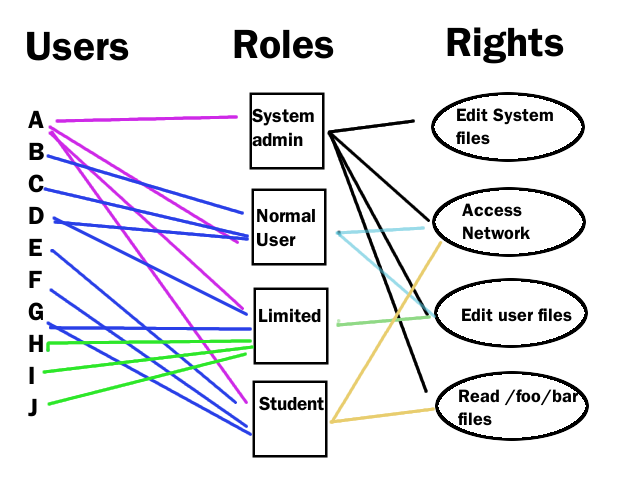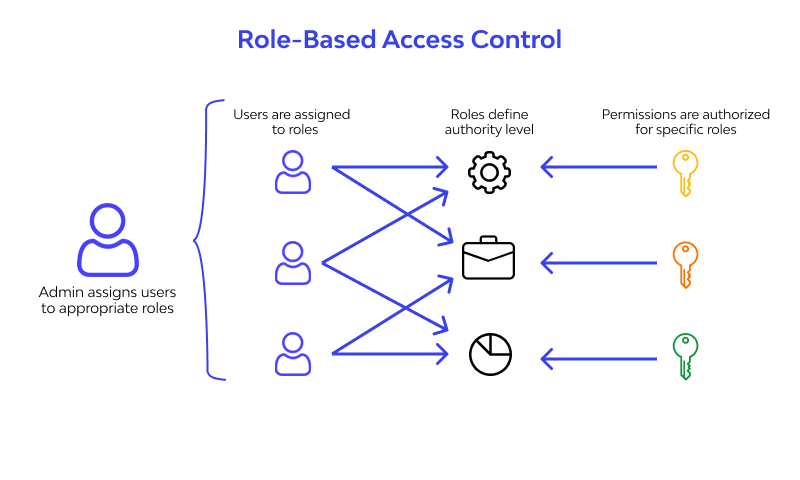
Role Based Access Control Ppt Powerpoint Presentation Styles Outfit Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
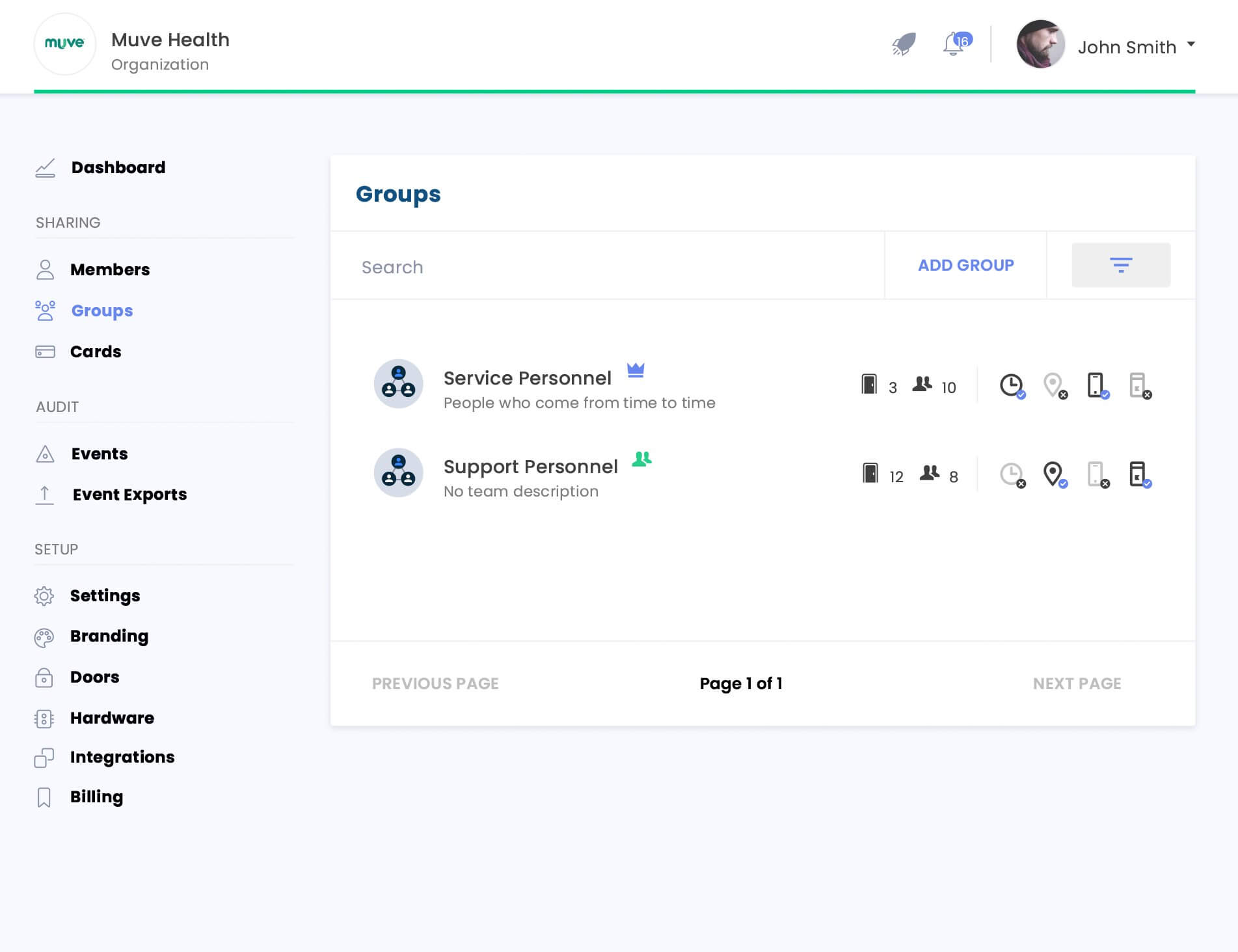
Role Based Access Control Data Mining Ppt Powerpoint Presentation File Professional Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates


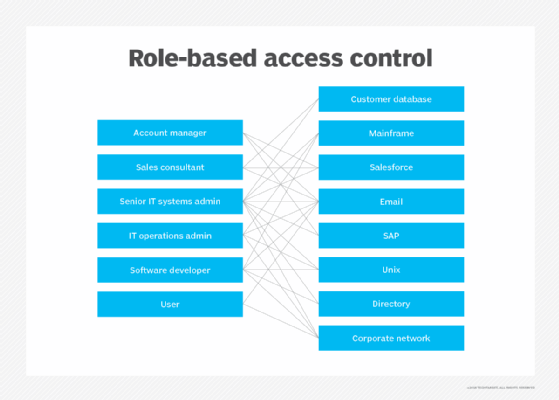



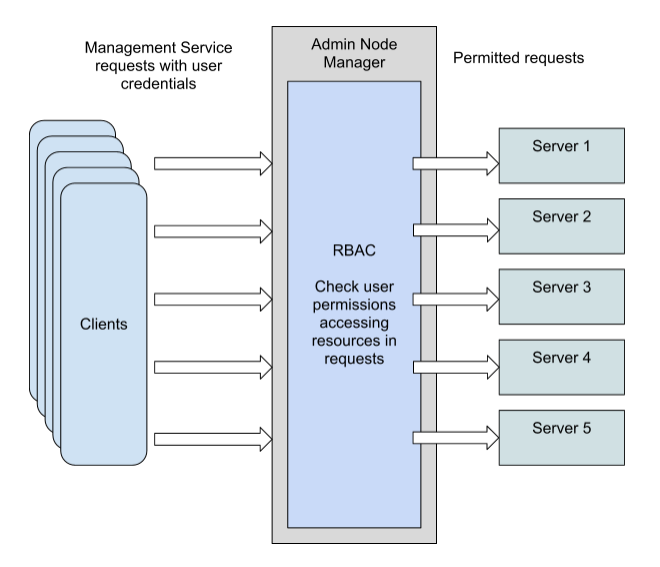
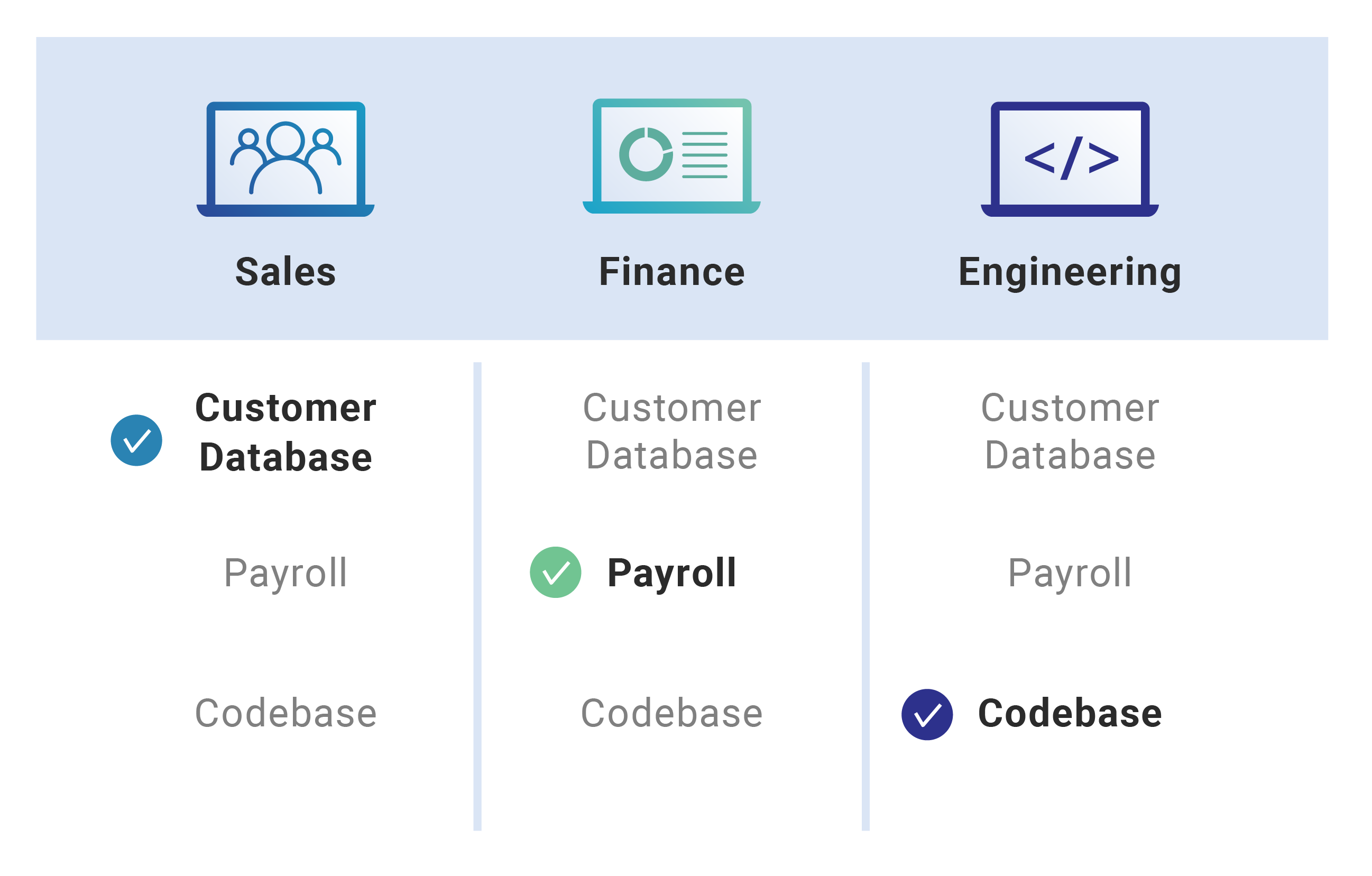
.png?width=687&name=RBAC_blog_diagram%20(2).png)