privacy - Best Practice: ”separate ssh-key per host and user“ vs. ”one ssh- key for all hosts“ - Information Security Stack Exchange
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples

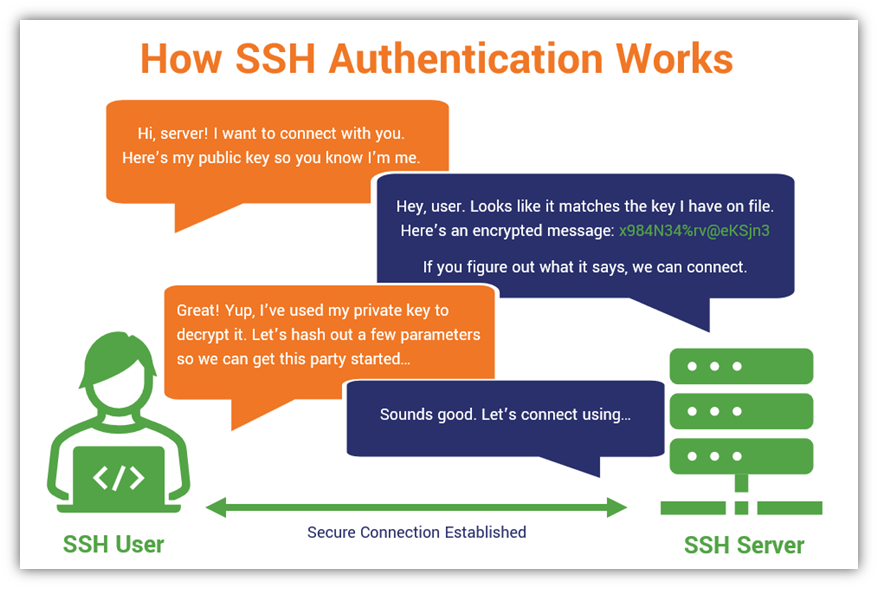
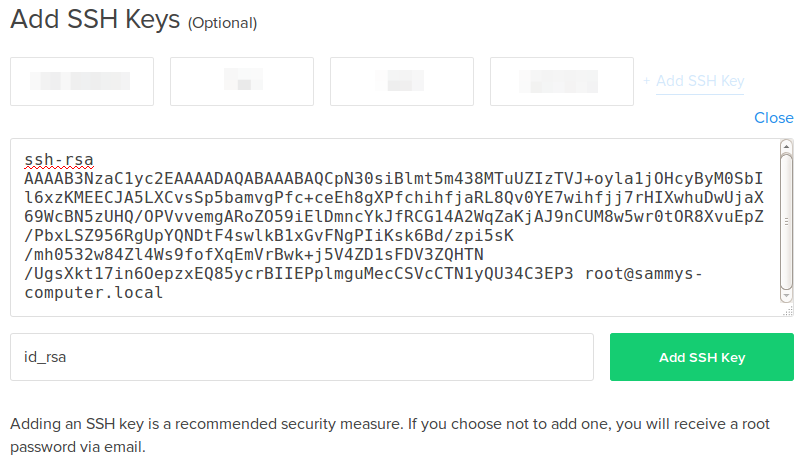
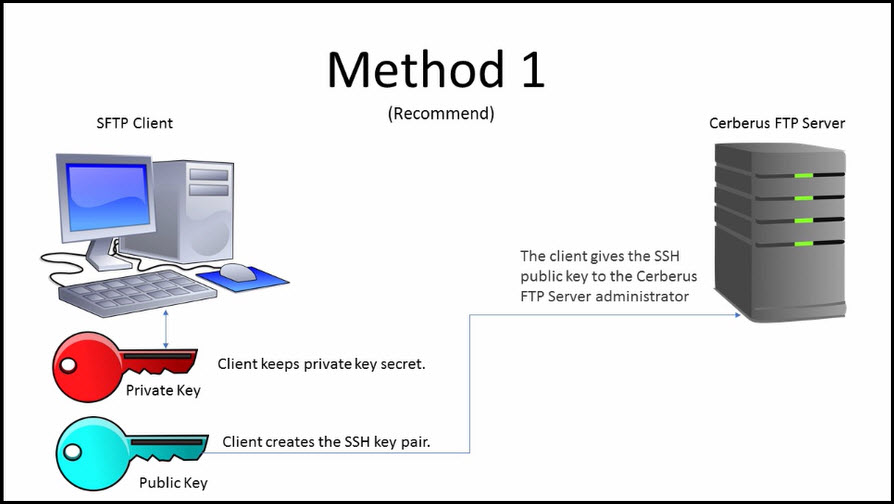
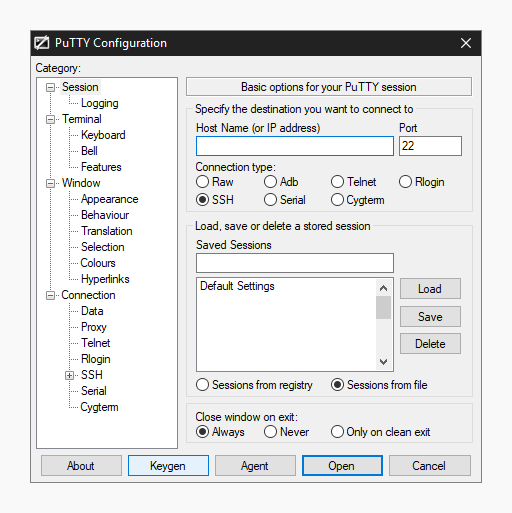
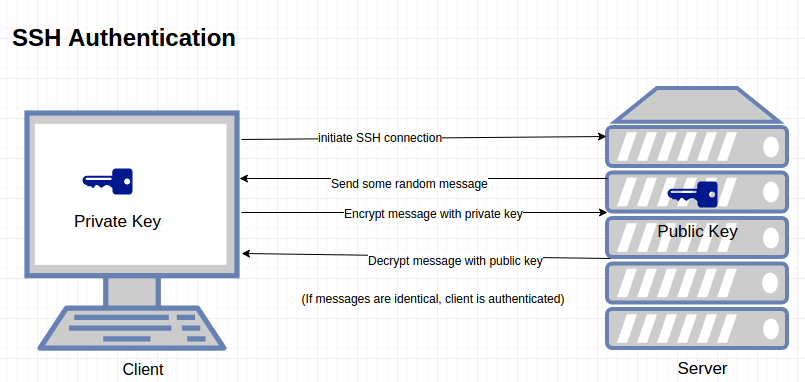
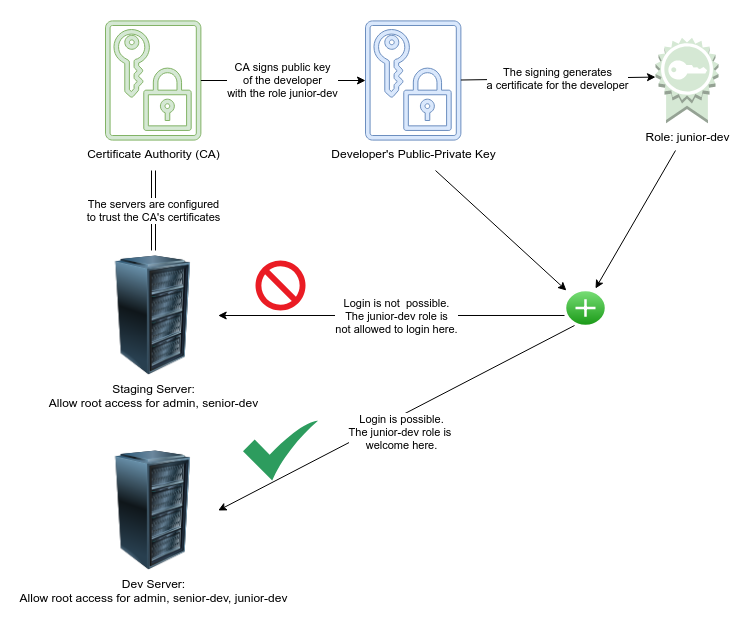
SSH keys authenticate users and hosts in SSH. They are used for single sign-on and machine-to-machine access. Security and convenience!