A novel method of S-box design based on discrete chaotic maps and cuckoo search algorithm | SpringerLink

Multilevel information fusion for cryptographic substitution box construction based on inevitable random noise in medical imaging | Scientific Reports

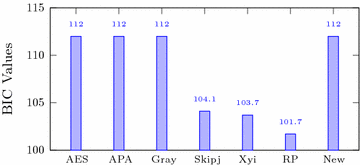
Bit independence criterion (BIC) values comparison for different S-boxes | Download Scientific Diagram
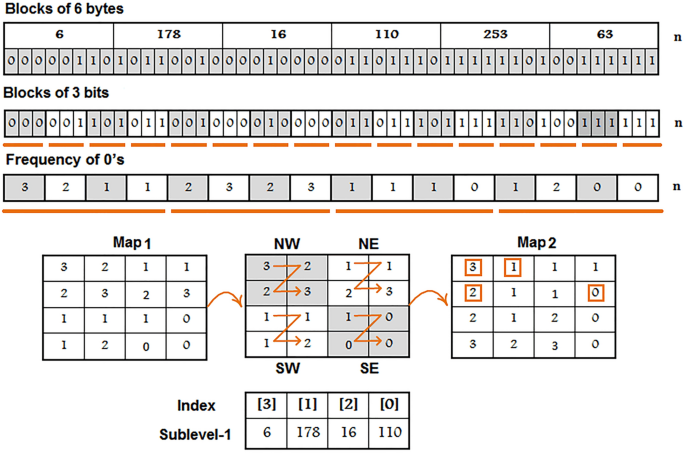
Multilevel information fusion for cryptographic substitution box construction based on inevitable random noise in medical imaging | Scientific Reports

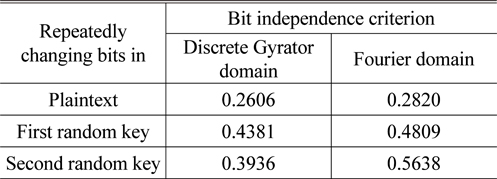
Comparison of Bit independent criterion (BIC)-nonlinearity (NL) with... | Download Scientific Diagram

Multilevel information fusion for cryptographic substitution box construction based on inevitable random noise in medical imaging | Scientific Reports
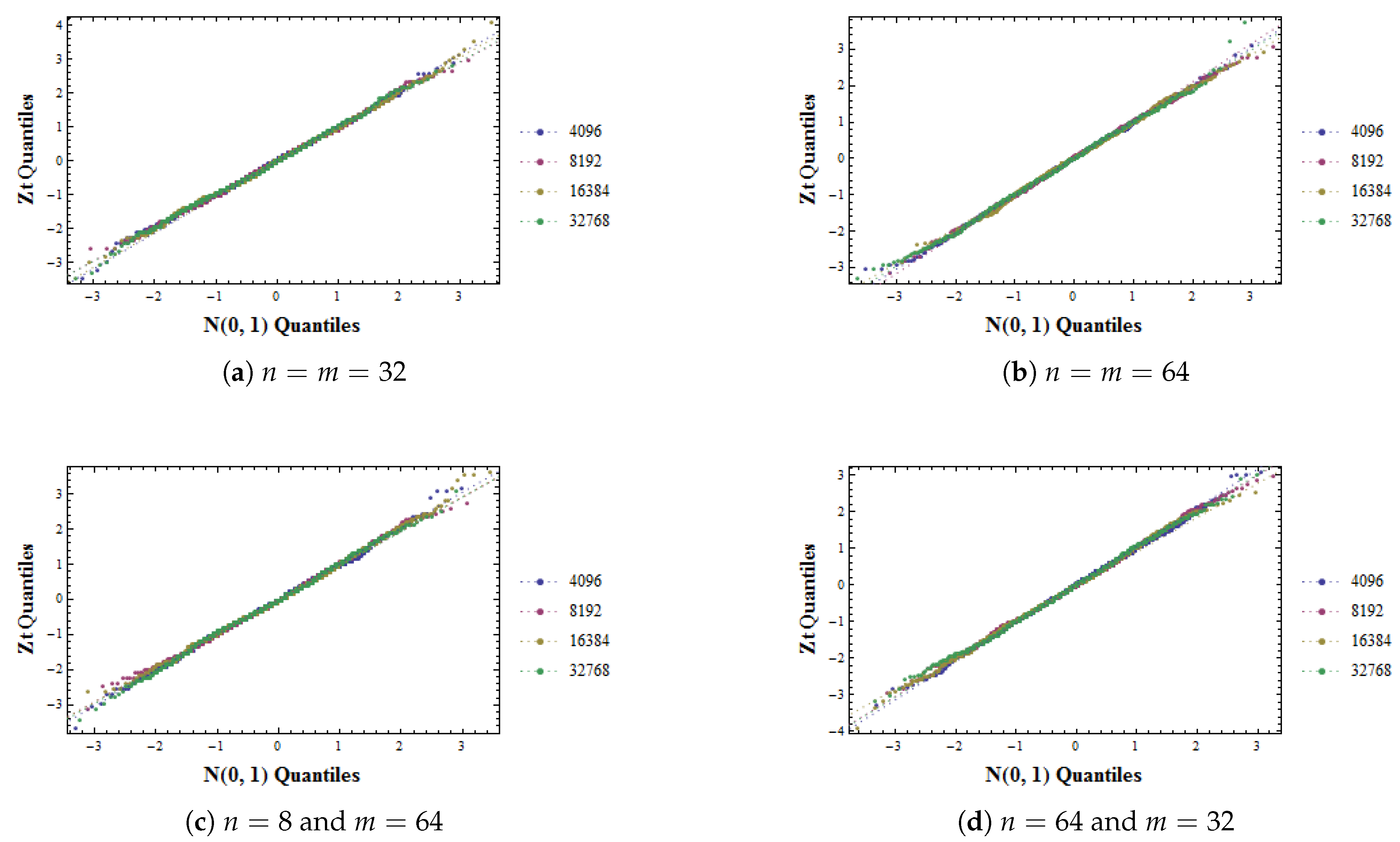
![PDF] Avalanche and Bit Independence Properties for the Ensembles of Randomly Chosen n × n S-Boxes | Semantic Scholar PDF] Avalanche and Bit Independence Properties for the Ensembles of Randomly Chosen n × n S-Boxes | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/187c14aaae1ef93090716c37d79dbe0b5ff41178/5-Figure2-1.png)
PDF] Avalanche and Bit Independence Properties for the Ensembles of Randomly Chosen n × n S-Boxes | Semantic Scholar
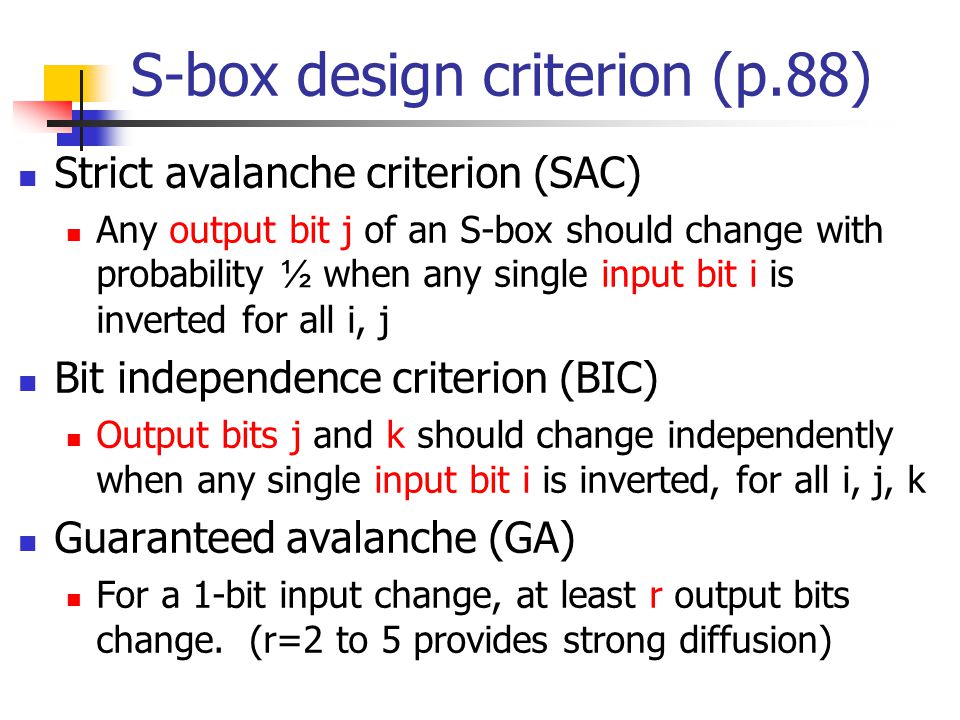
Chap. 5: Advanced Encryption Standard (AES) Jen-Chang Liu, 2005 Adapted from lecture slides by Lawrie Brown. - ppt download

Multilevel information fusion for cryptographic substitution box construction based on inevitable random noise in medical imaging | Scientific Reports

To Study the Effect of the Generating Polynomial on the Quality of Nonlinear Components in Block Ciphers