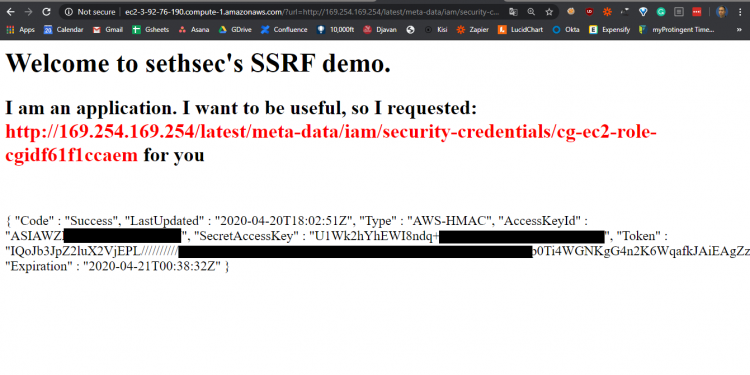
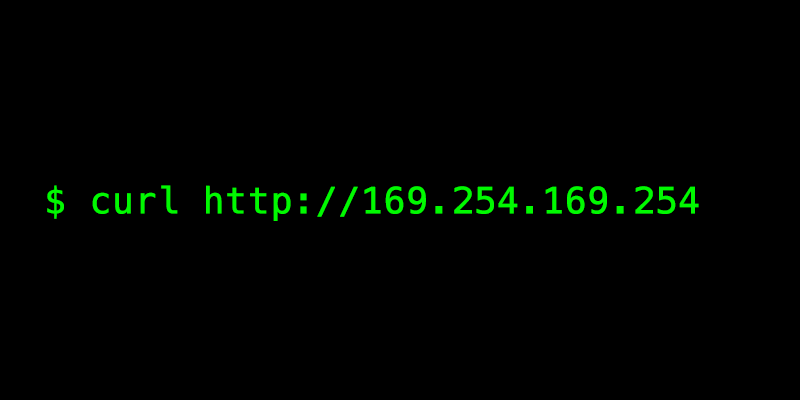
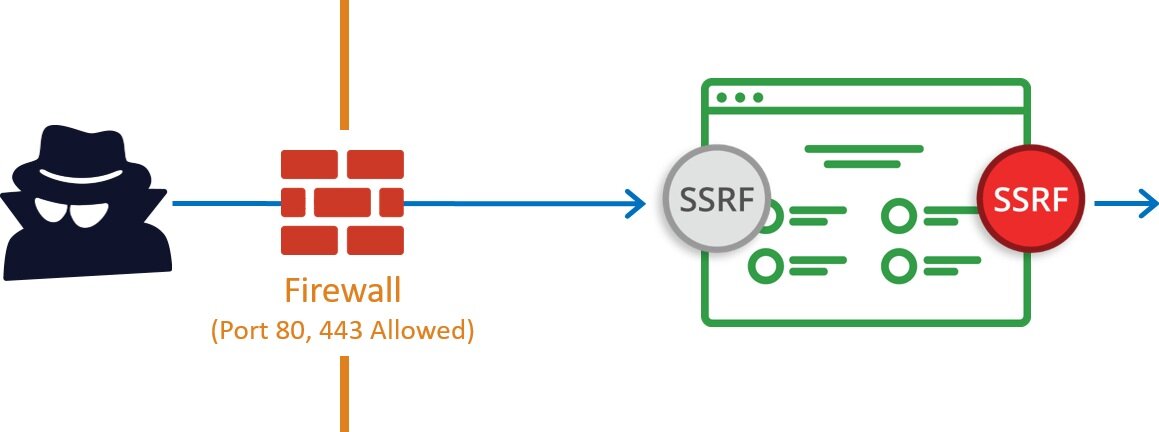
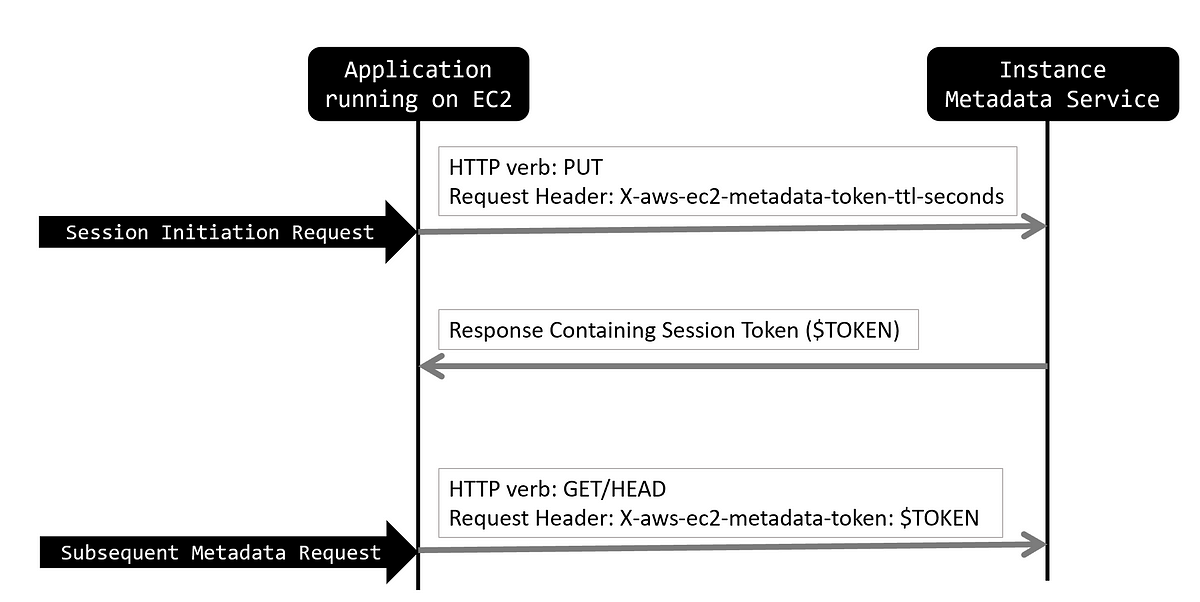
Active Defense - Dynamically Locking AWS Credentials to Your Environment | by William Bengtson | The Startup | Medium
Netflix Information Security: Preventing Credential Compromise in AWS | by Netflix Technology Blog | Netflix TechBlog

Get started with automated metadata extraction using the AWS Media Analysis Solution | AWS Machine Learning Blog

Hunting for Capital One Breach TTPs in AWS logs using Azure Sentinel - Part I - Microsoft Tech Community

A guide to automating HashiCorp Vault #2: Authenticating with instance metadata | by Etiene Dalcol | Gruntwork