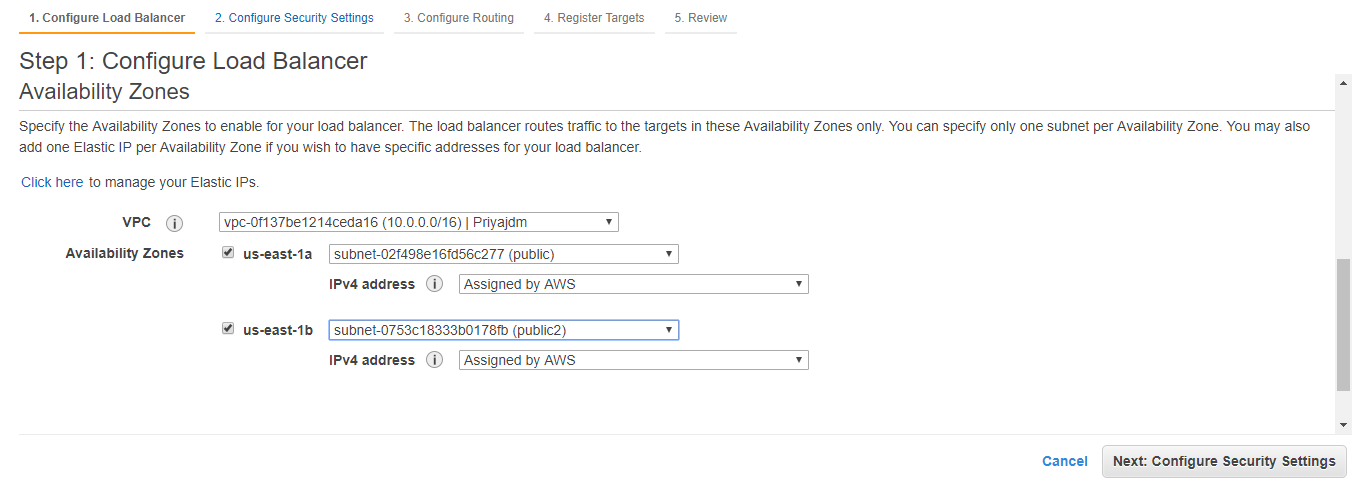
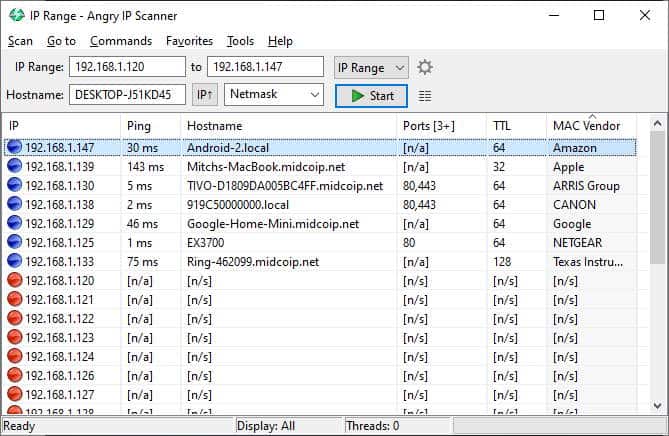
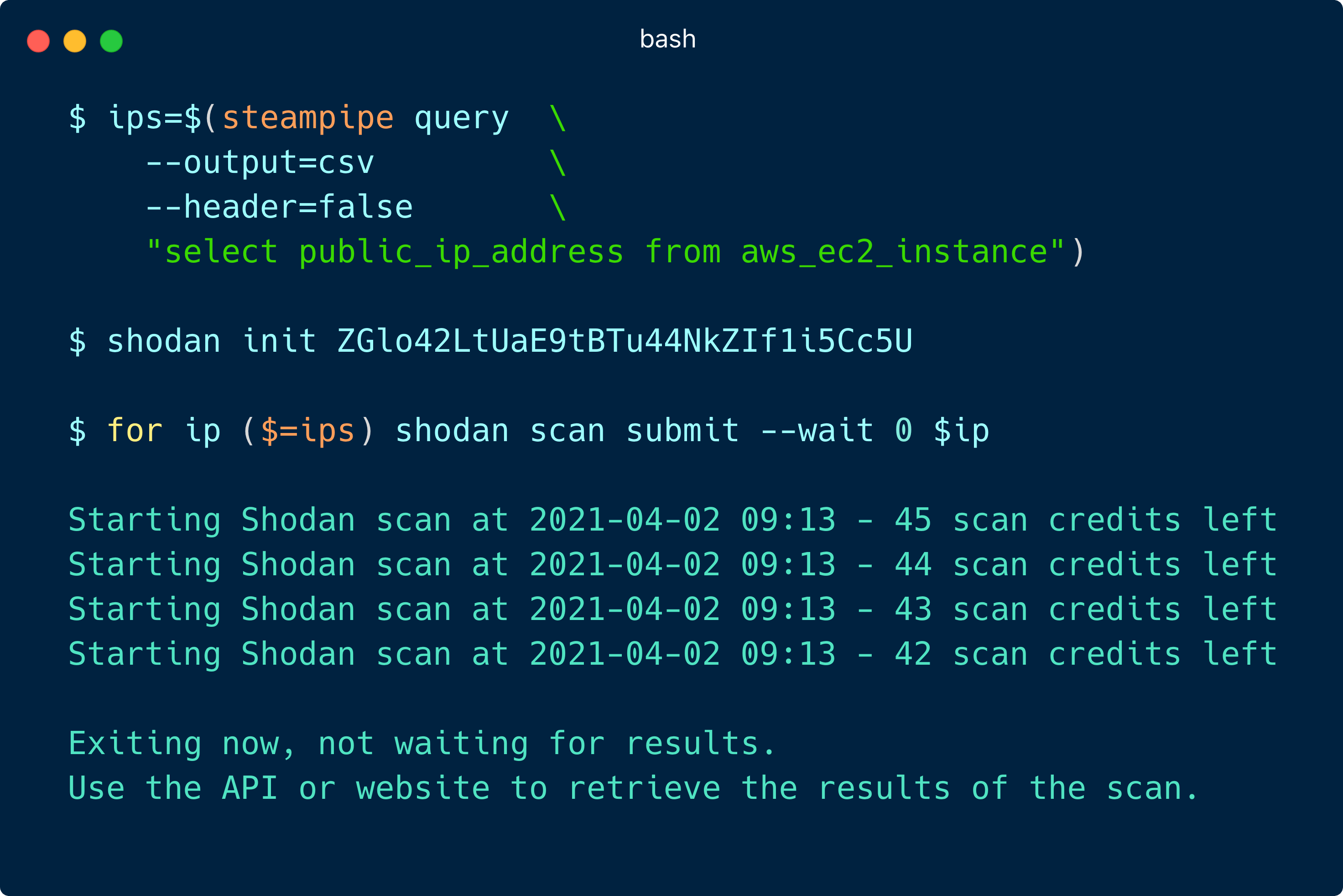
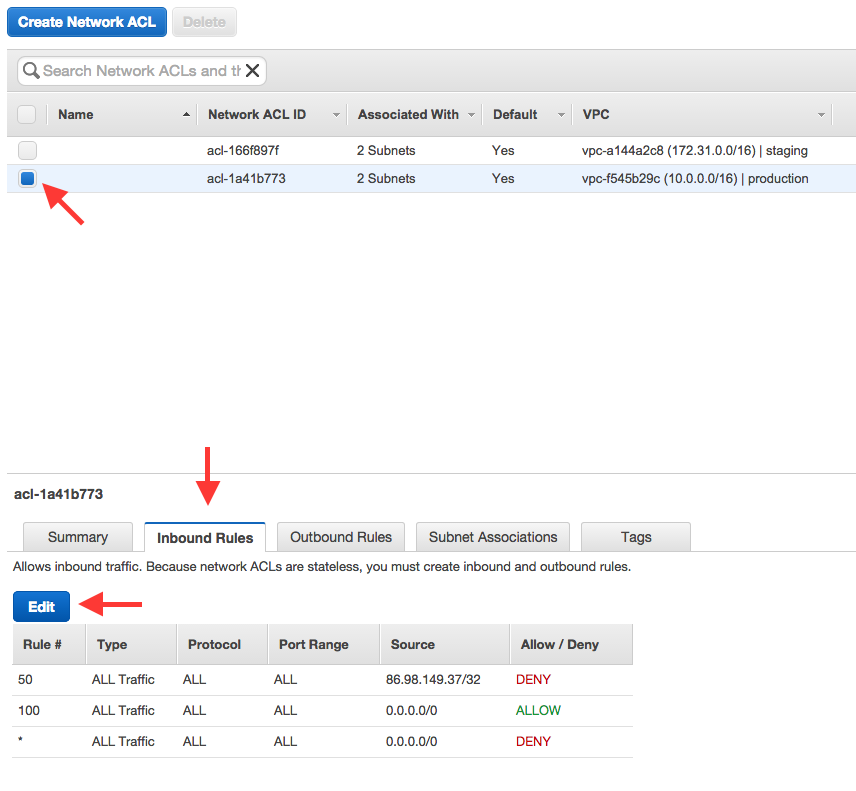
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog

Automatically block suspicious traffic with AWS Network Firewall and Amazon GuardDuty | AWS Security Blog

Detect suspicious IP addresses with the Amazon SageMaker IP Insights algorithm | AWS Machine Learning Blog

Geo-Recon - OSINT Tool To Fast Track IP Reputation And Geolocaton Look Up For Security Analysts - GeeksforGeeks

How to Sideload Apps onto an Amazon Fire TV or Fire TV Stick using an Android Phone or Tablet | AFTVnews

How to manually configure the IP address or DNS server on an Amazon Fire TV or Fire TV Stick | AFTVnews

How to visualize multi-account Amazon Inspector findings with Amazon Elasticsearch Service | AWS Security Blog

Automatically block suspicious traffic with AWS Network Firewall and Amazon GuardDuty | AWS Security Blog